Effortlessly manage inactive guest accounts in Microsoft Entra ID with Guests
On the internet and in Microsoft forums, there’s a wealth of discussions surrounding how Microsoft 365 administrators can easily identify inactive guests within Microsoft Entra (formerly Azure Active Directory) and, if necessary, deactivate or delete those who haven’t logged in within the last 90 days or a similar timeframe.
View guests’ last sign-in and activity
In the user view of the Microsoft Entra admin center, administrators can access the audit and sign-in logs of guest identities for the past 7 days. However, this doesn’t effectively address the challenge. Microsoft recommends using the Microsoft Graph Reporting API to obtain detailed sign-in information. The use of the reporting API requires Microsoft Entra ID P1 or P2 licenses. However, even with these licenses in place, the Microsoft Entra admin center doesn’t offer an easy way to oversee or filter guests who haven’t logged in, for example, within the last 90 days.
Identify, block, or delete inactive guests by last sign-in date
For skilled system administrators, utilizing the Microsoft Graph activity logs can be a viable solution. With Guests, we’ve aimed to provide a simple and more straightforward way to access a summary of all guests and their latest login dates, making it accessible to administrators of all experience levels.
When you navigate to the guest list in the Guests admin center, you’ll find a column displaying the last sign-in date of each guest. Based on this information, Microsoft 365 administrators can easily identify inactive guest accounts and, if necessary, block their access or delete them permanently.
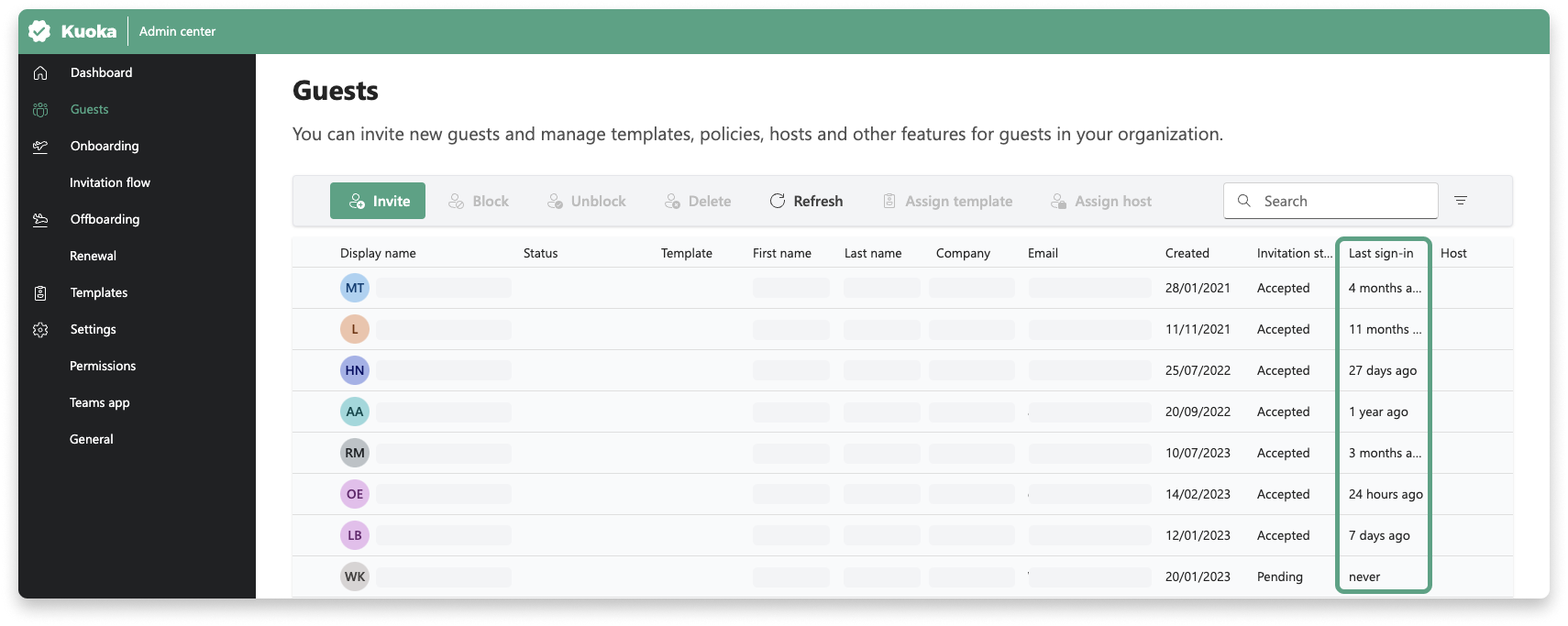
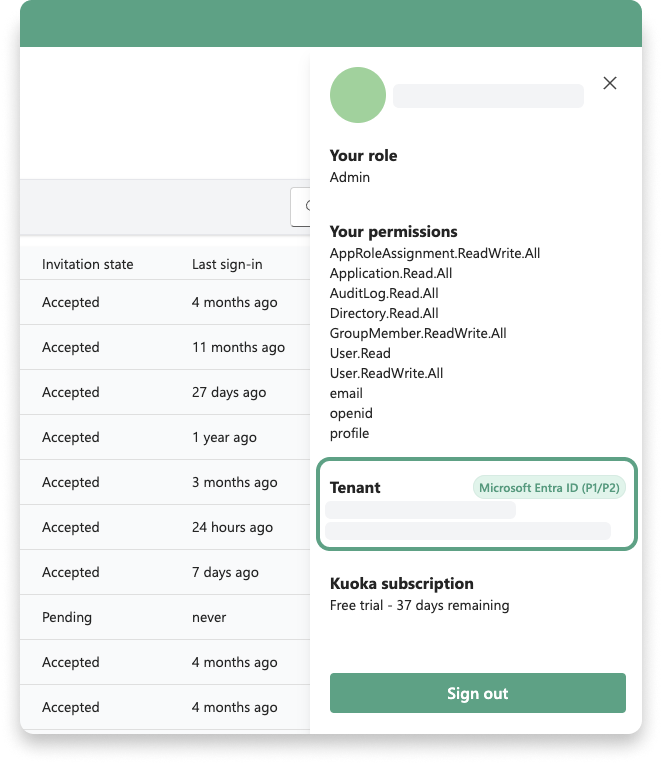
This feature leverages the Microsoft Graph for querying activity reports and, as a result, it functions in Guests only when the required Microsoft Entra ID P1 or P2 licenses are available in the tenant. You can easily verify this in Guests by opening the User Info in the Guests Admin Center. If you see a “Microsoft Entra ID P1/P2” indicator there, the column displaying the last sign-in information will be visible. If the indicator is not present, the column won’t be visible either.
Ready to dive in?
No credit card required